-
Notifications
You must be signed in to change notification settings - Fork 12
Multi or Cross Tenant Deployment
For the default (and most common) deployment, Call Record Insights is deployed to an Azure Subscription associated with the same Microsoft Entra ID Tenant that is being monitored.
However, when that shared tenant context is not possible, it is possible to deploy Call Record Insights to work in either a Cross-Tenant or Multi-Tenant configuration.
Example:
-
Development deployment with Production data being monitored
-
Single deployment with multiple subsidiary tenants being monitored
Since the default deployment uses Managed Identity for all Microsoft Graph authentication, this will not work, as the identity would only have permissions to access data from the tenant which owns the Identity.
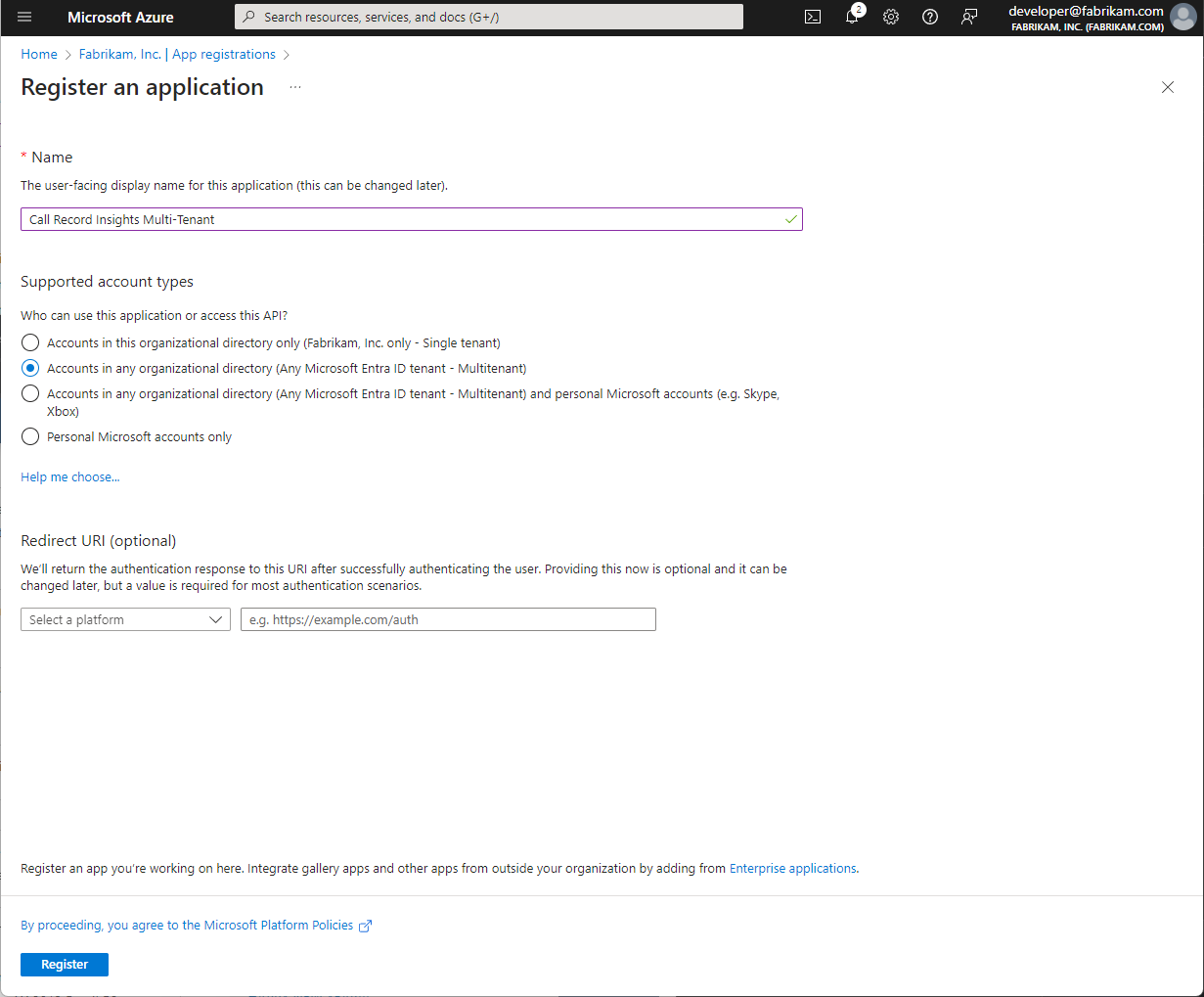
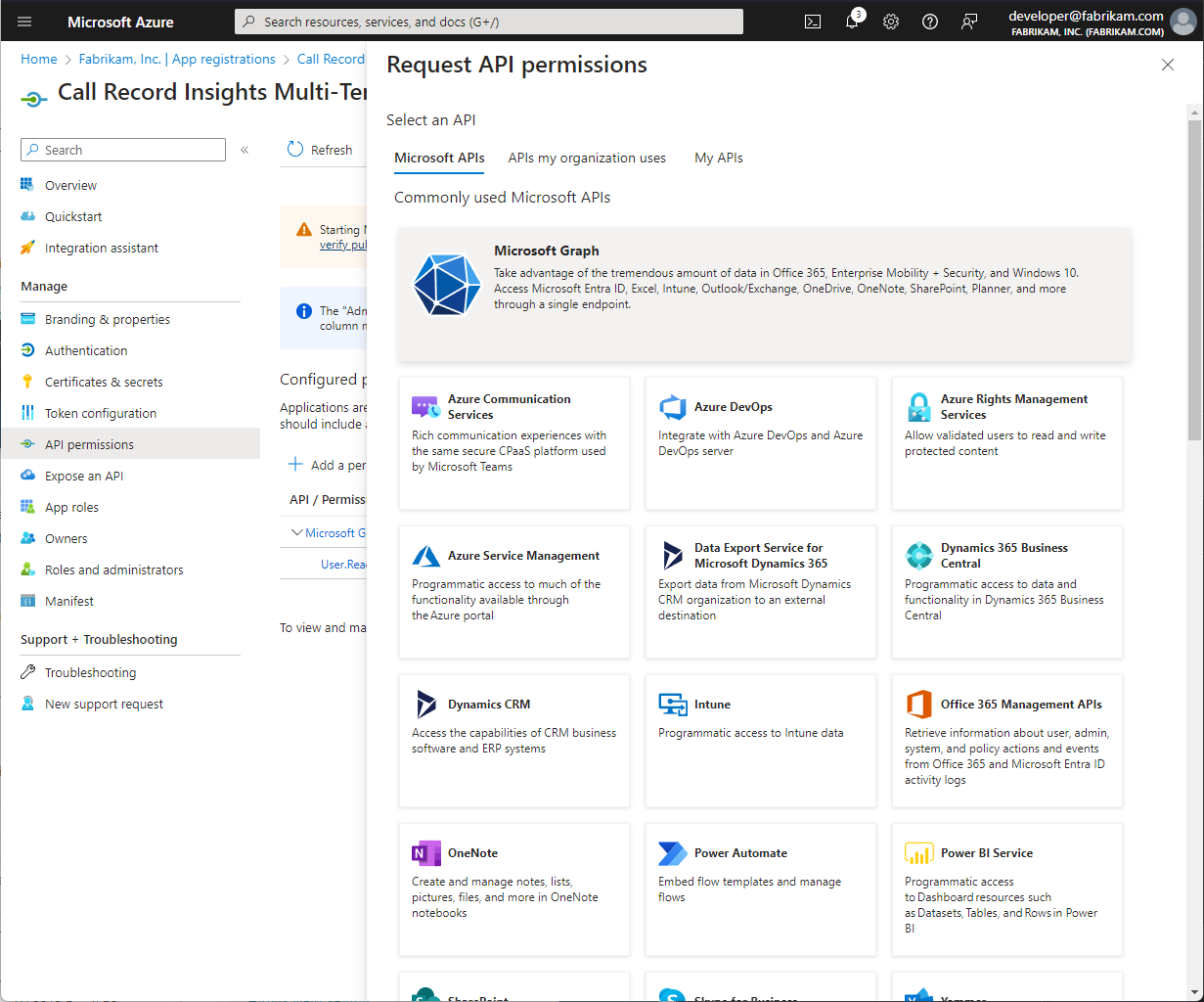
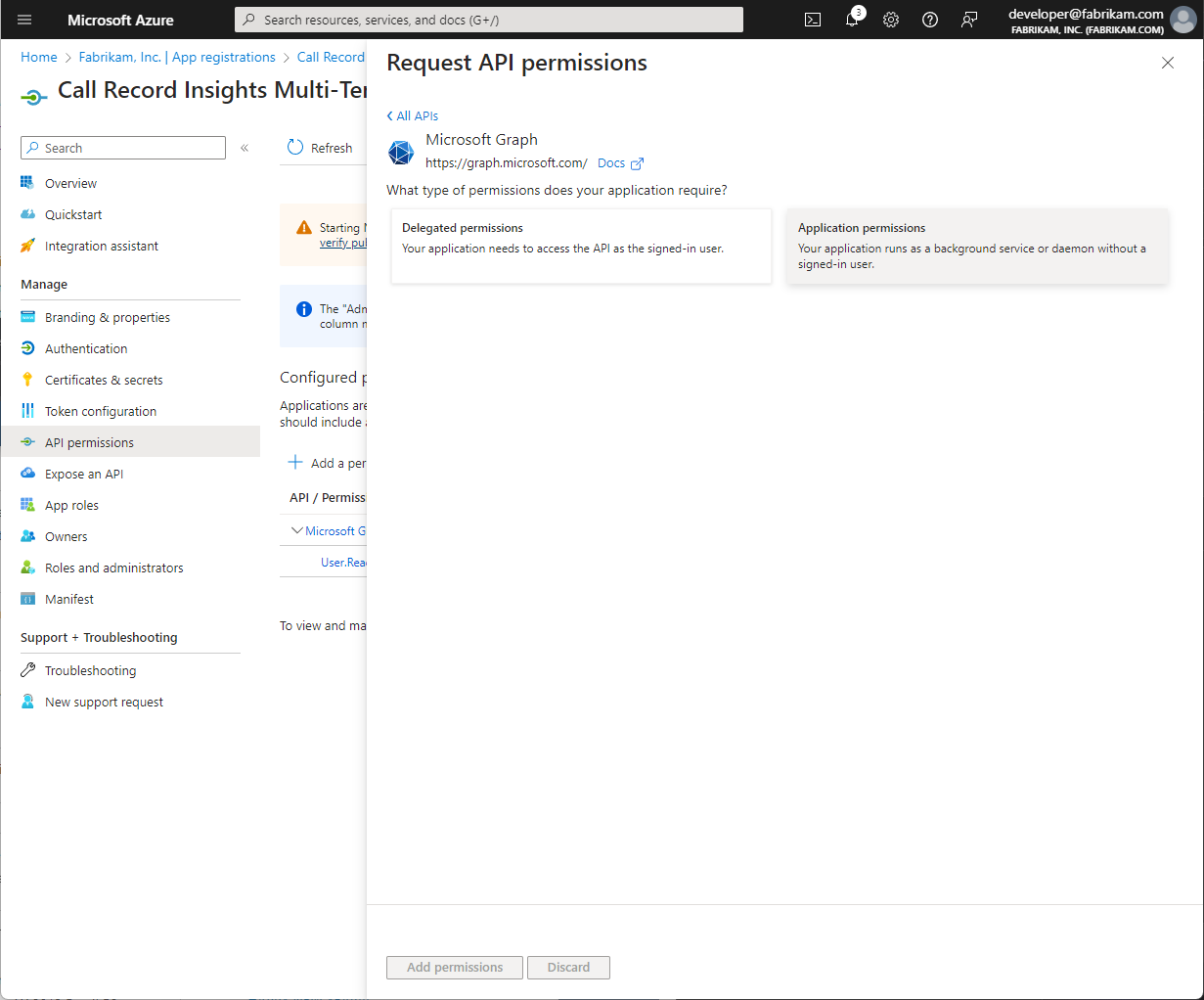
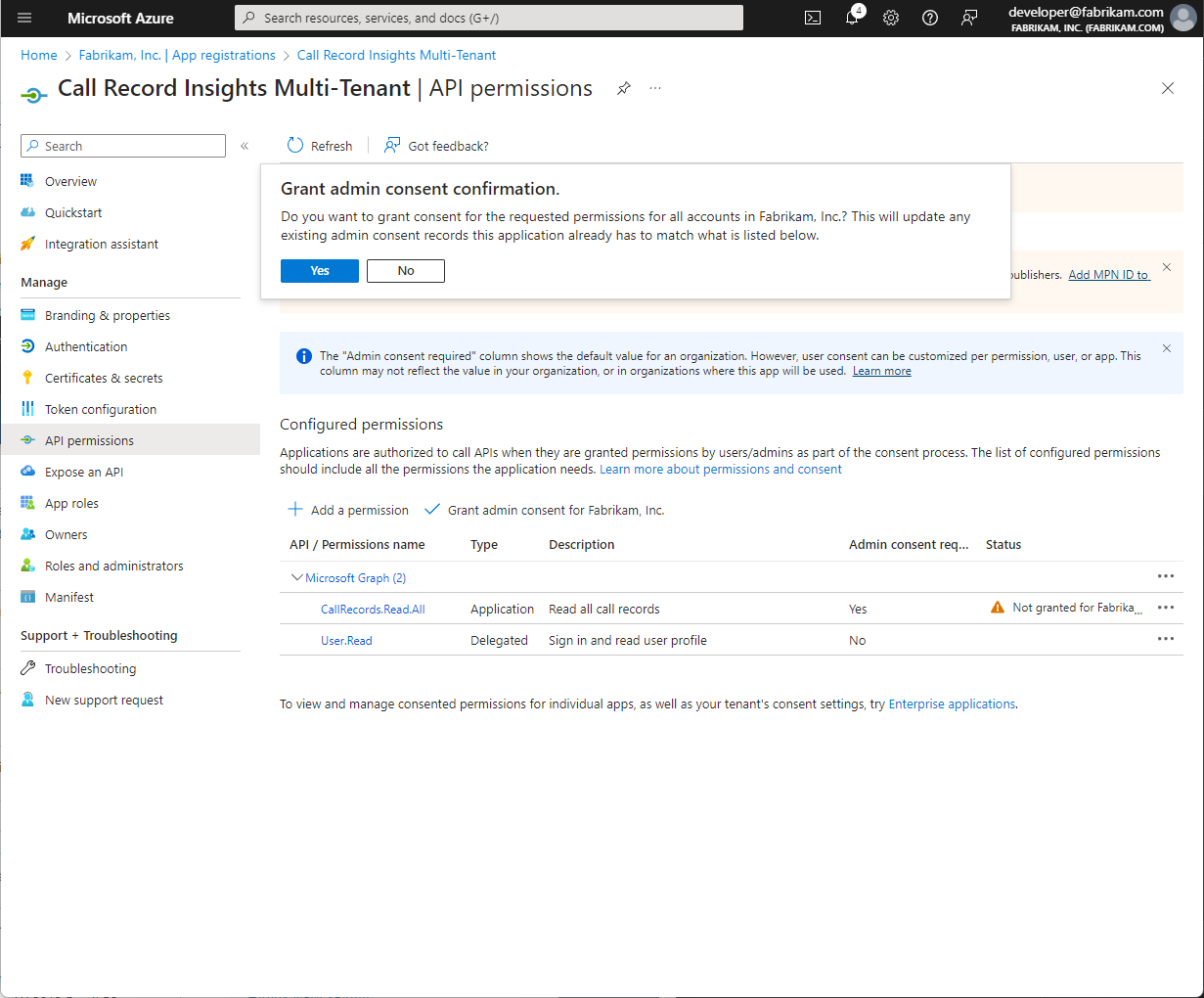
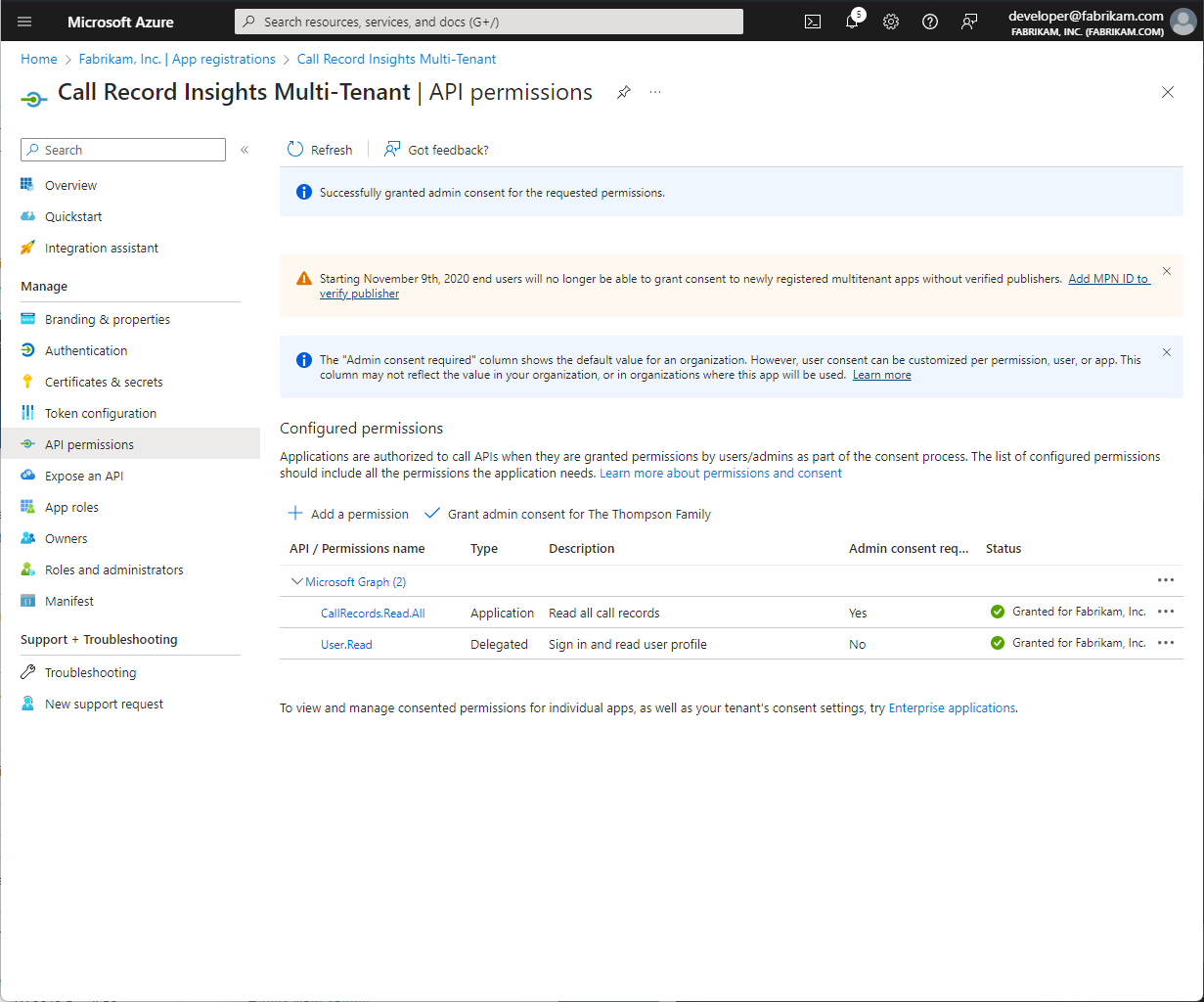
By using Microsoft Entra ID App authentication, we can authenticate against external tenants that have been properly configured and consented.
Note
Be sure to select Accounts in any organizational directory (Any Microsoft Entra ID - Multitenant)

Note
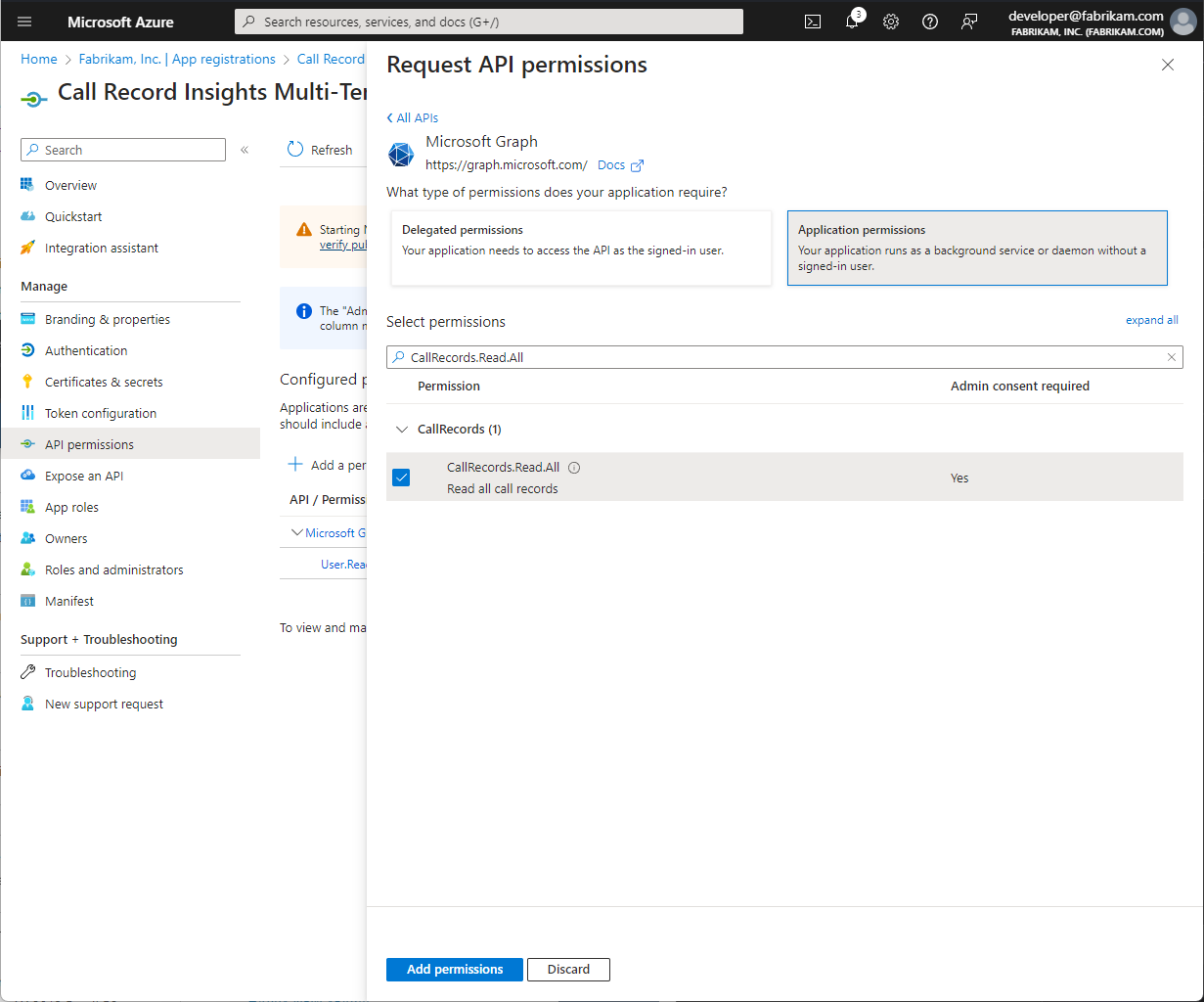
This is only necessary if the Microsoft Entra ID Tenant where Call Record Insights is deployed is being monitored
This is unneeded if Call Records for this tenant are unwanted
Note
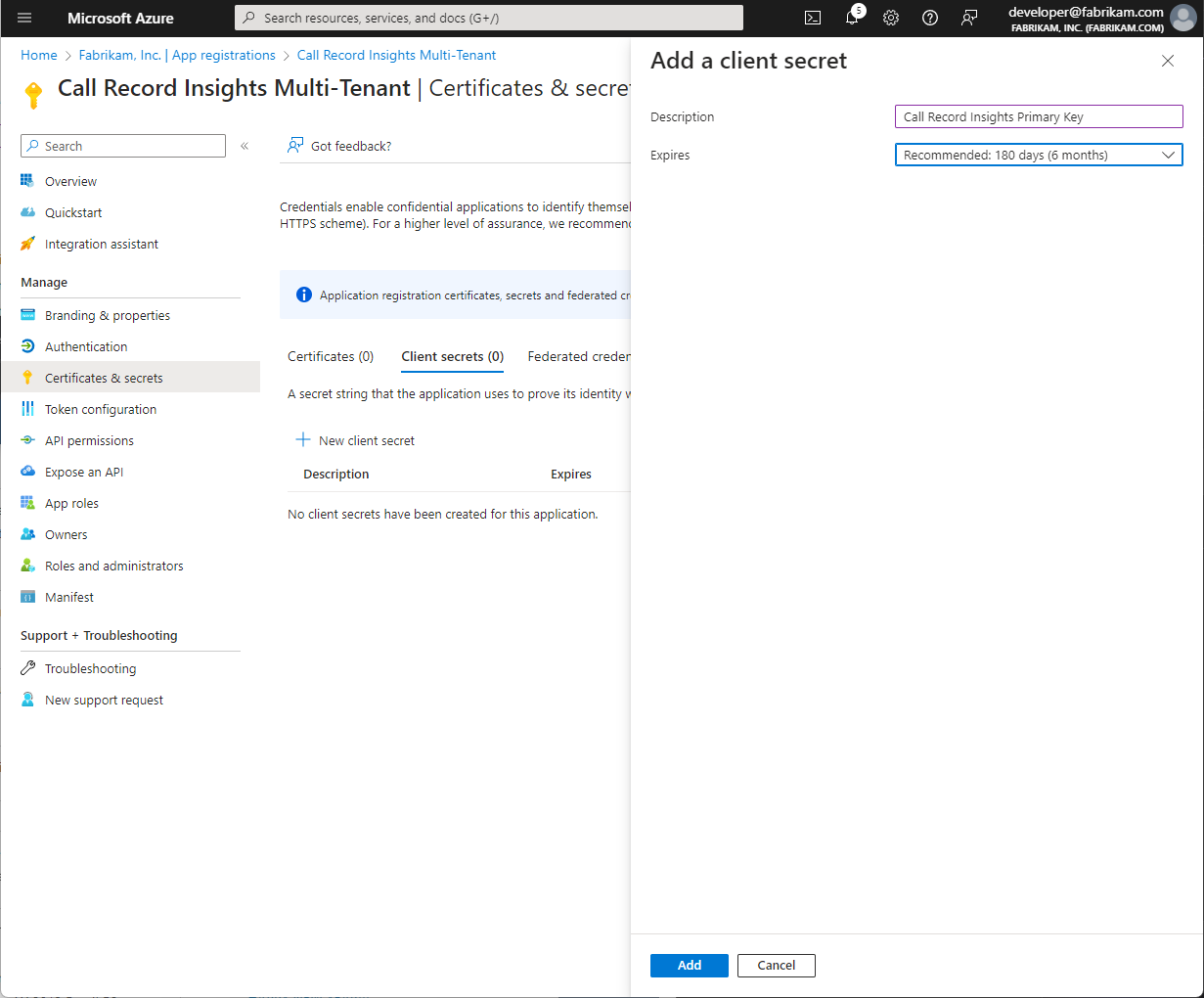
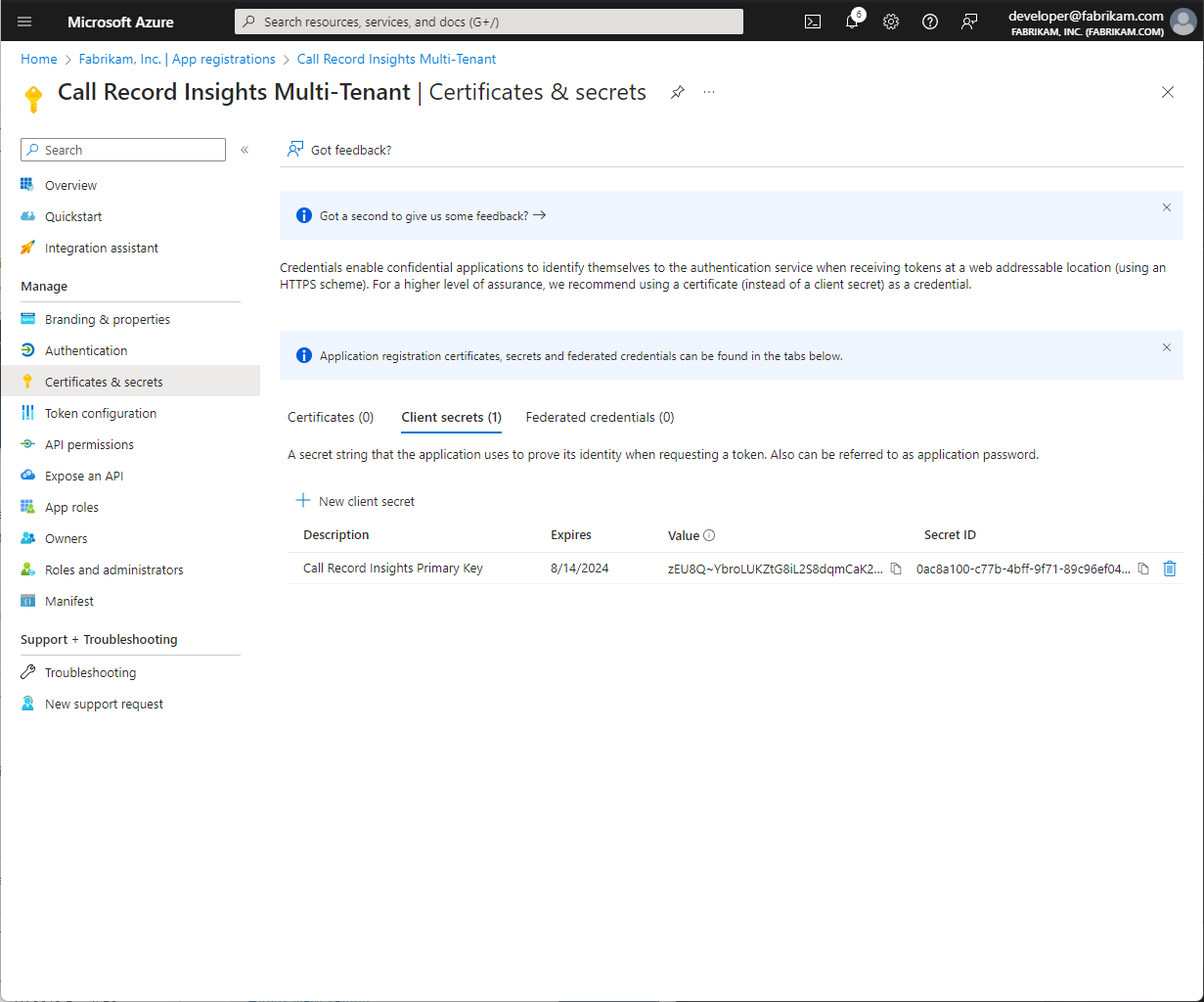
Client Certificates can also be used
It is recommended that this is not done via the portal but instead managed and stored within the configured Azure Key Vault used by Call Record Insights
Note
If this Secret or Certificate Expires or is revoked, Call Record Insights will no longer be able to monitor Call Records until renewed.
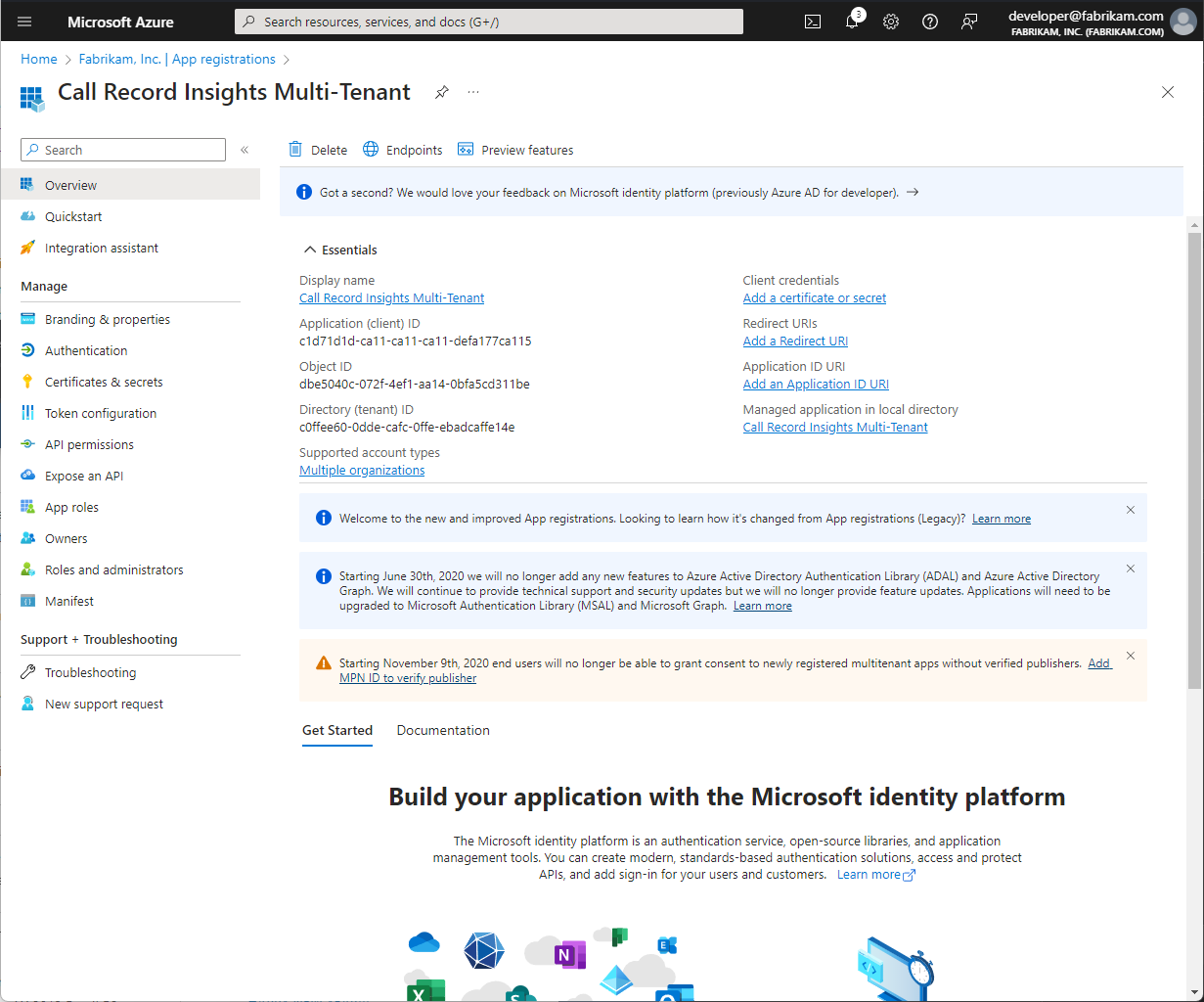
$MultiTenantAppClientId = 'c0ffee60-0dde-cafc-0ffe-ebadcaffe14e' # This should be the Application (client) ID for the app registration
Connect-MgGraph -Scopes Application.ReadWrite.All
$NewSPN = New-MgServicePrincipal -AppId $MultiTenantAppClientId
Write-Host "Go To https://portal.azure.com/#view/Microsoft_AAD_IAM/ManagedAppMenuBlade/~/Permissions/objectId/$($NewSPN.Id)/appId/$MultiTenantAppClientId to grant consent to the application for your tenant."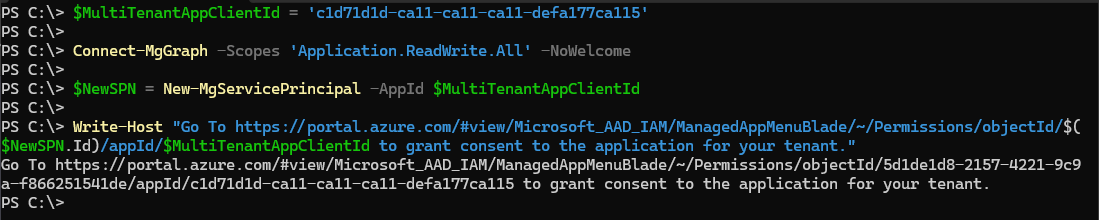
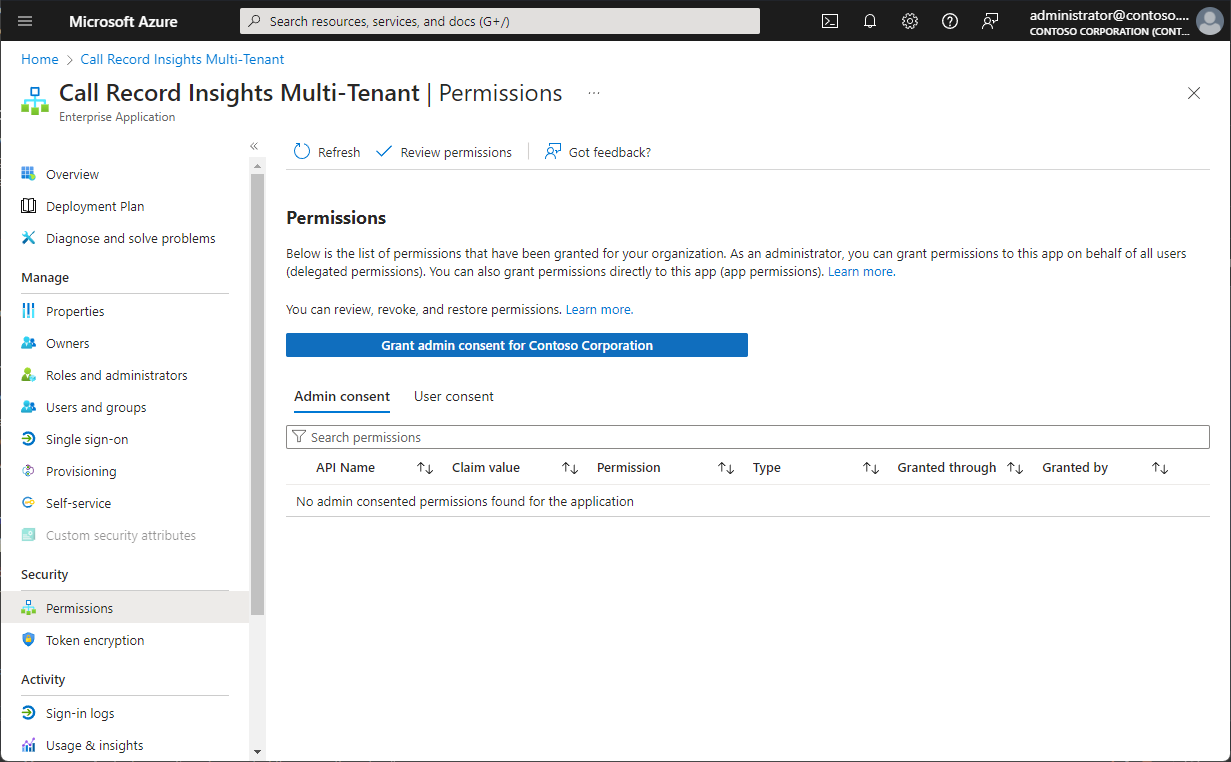
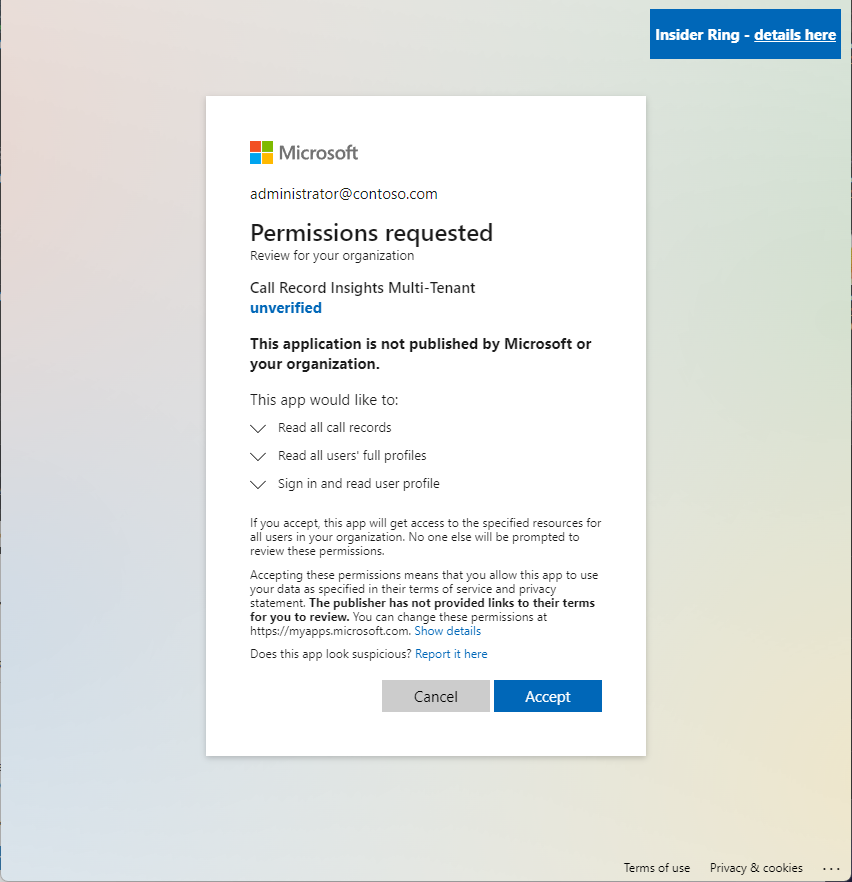
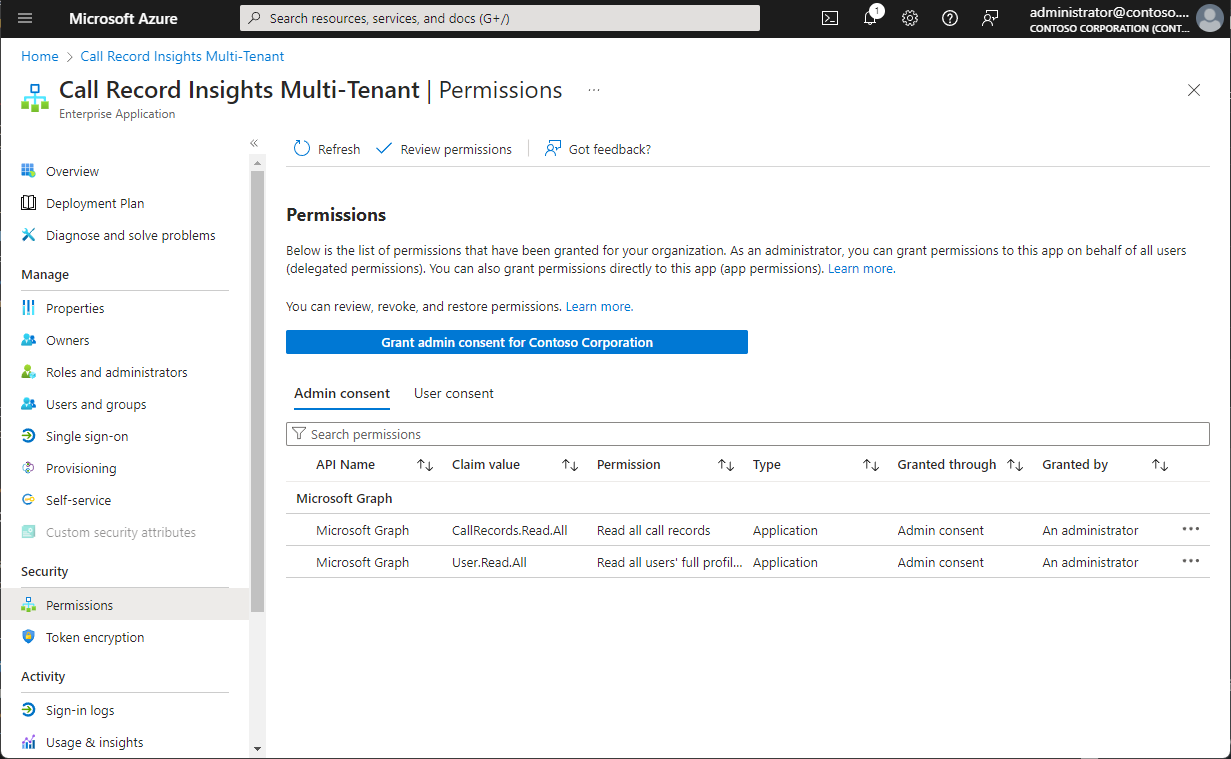
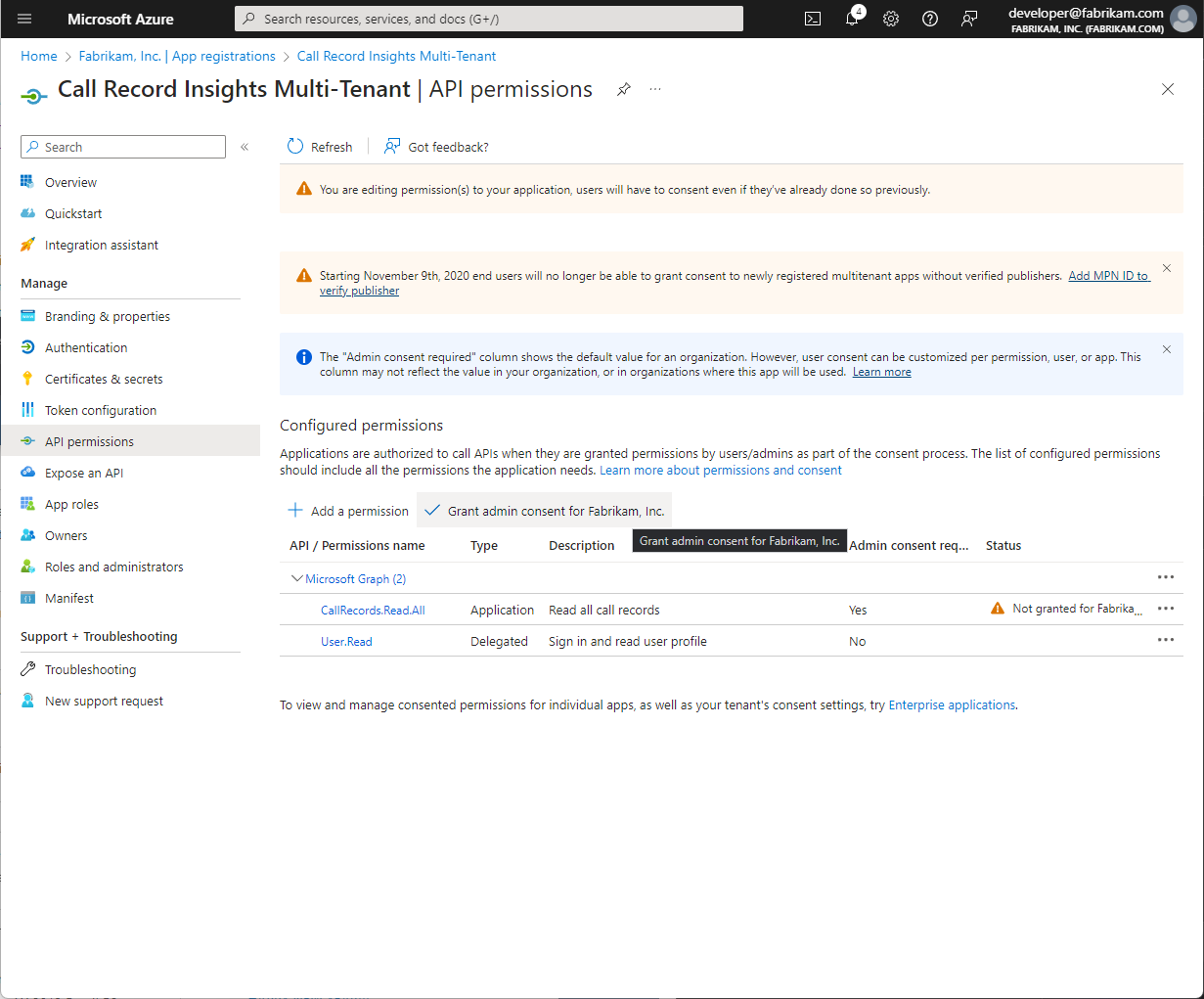
Ensure all monitored domains are present in the Monitored Tenant List.
If a domain is not listed in this configuration, it will not be monitored even if consent has been granted
If the local tenant is also monitored, be sure to include it in the configuration in addition to any external Tenants.
Enable Call Record Insights to use the App Registration
This is done in the Graph App Configuration, refer there for more information and example(s)