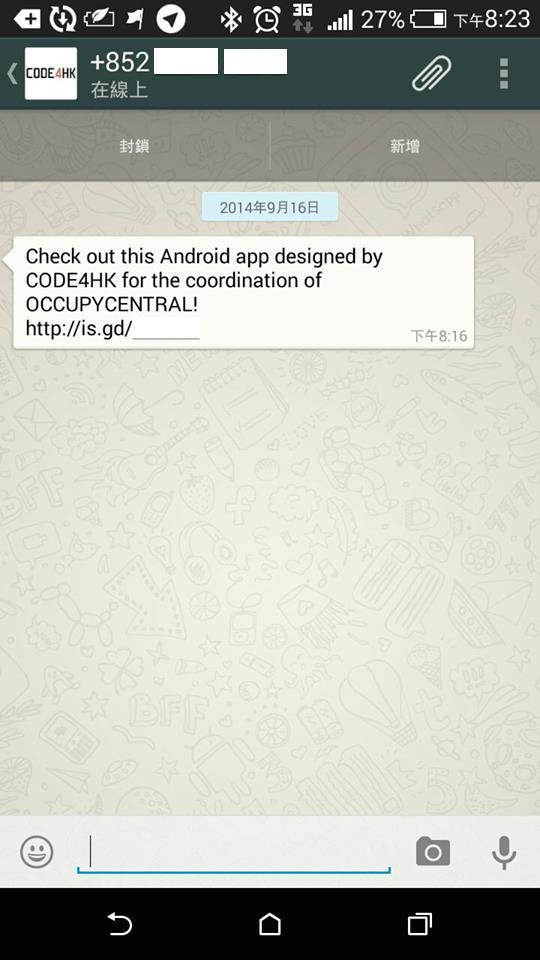
This App turned up being sent to Hong Kong Whatsapp users.
It claimed
Check out this Android app designed by CODE4HK for the coordination of OCCUPYCENTRAL! http://is.gd/****
This is a decompiled version of that, trying to work out what it does.
Use apktool v2.0.0rc1 (v1.5.x doesn't work with this)
$ apktool d code4hk.apk
Once I worked out assets/qq.xml was actually a hidden apk
I did the same with that
$ cp decompiled/assets/qq.xml qq.apk
$ apktool d qq.apk
When it boots it copies assets/qq.xml to the location "/sdcard/.qq/temp.apk". Thereby attempting to hijack your QQ app.
It hooks into any outgoing calls
<receiver android:name="com.v1.PhoneReceiver" android:priority="2147483647">
<intent-filter>
<action android:name="android.intent.action.PHONE_STATE"/>
<action android:name="android.intent.action.NEW_OUTGOING_CALL"/>
</intent-filter>
</receiver>
https://github.com/matthewrudy/fake-code4hk-app/blob/master/decompiled/AndroidManifest.xml#L64-L69
And seems to record them
And stores them at "/data/data/com.v1/temp.amr"
It uses baidu to gather location data
iget-object v2, v0, Lcom/v1/StreamService;->m:Lcom/baidu/location/LocationClient;
invoke-virtual {v2}, Lcom/baidu/location/LocationClient;->start()V
The external IP address and port is set to "61.36.11.75" and "1430" respectively.
This is configured from assets/config.dat for the basic app
And the same for the fake qq app's assets/config.dat