-
Notifications
You must be signed in to change notification settings - Fork 21
Deobfuscate Skater protected .NET assemblies
In this article, we will study an executable protected by Skater .NET Obfuscator. .NET deobfuscate means deobfuscating of .net exe files, which were developed by visual studio.
Let’s start from decompiling the .NET file. It is a heavily obfuscated .NET executable and it could be more difficult to crack. The executable is written in .NET so we can decompile it using some of the popular tools made for this purpose (.NET Refractor, JustDecompile, etc).
As we can see, the code is obfuscated: functions have been entangled, variables/classes/methods got meaningless names. Also the spaghetti code inside the obfscted.exe contains a lot of junk instructions and that is difficult to follow. Even applying a known tool for .NET deobfuscation did not helped much.
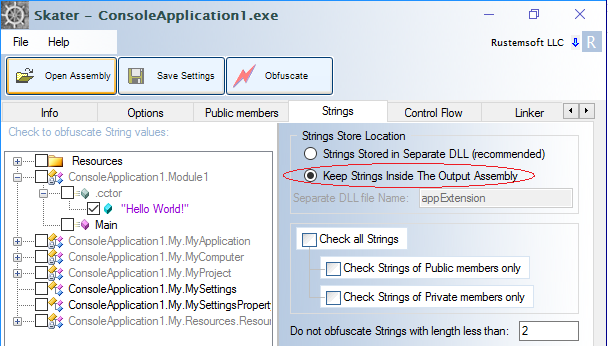
Strings obfuscated by Skater
One of the most common practices of backpedaling analysis is obfuscation of string values. In .NET assemblies, String obfuscation is most often realized by applying a series of mindless parameters to a deobfuscation algorithm which then returns the deobfuscated string to a method. Practically, it must run like that since built-in .NET functions are unable to accept strings in an obfuscated format. String deobfuscation in .NET assemblies is hard to implement.
Skater’s arsenal has a particular string protection method that is practically impossible to recover. It protects source code algorithm by coding Strings in native code while preserving the user interface in .NET. Skater extracts String values and uploads into C++ source code. Then it compiles the C++ written code and locate the resulting machine-code library (appExtension.dll) file in the output directory. When our final obfuscated assembly runs it will be calling this DLL through platform invoke (Pinvoke Interop) as that is the shortcut way to call the machine-code from .NET app.
Please read how to protect .NET String values by hiding them into machine code DLL.
Conclusion
The current world of .NET deobfuscation does not have a lot of enlightened software tools. There are only few of them presented. The end result of deobfuscation should be simple, human-readable code that is logically equivalent to the original obfuscated source code. Skater obfuscation prevents from making the overall .NET source code much more readable and easier to comprehend. Skater persistently and successfully struggles with deobfuscation.